Fun with LCDs and Visual Cryptography
Introduction
Did you know that you can combine two LCDs in a way that lets you see the XOR of their contents?
Motivating Problem
Imagine a communications device made up of two mutually-untrusted halves. The halves are built with components sourced from two completely separate supply chains. We want the property that a remote adversary can never see a decrypted message, even if one of these halves contains a critical vulnerability.
How could such a device ever display a decrypted message to the user? At the end of the day, we need to combine key material and ciphertext, decrypt the message, and show it on a display. If a single chip ever sees both the key and the ciphertext, or if the plaintext ends up on a single display component, that represents a single point of failure in our design. Is there any way around this?
Visual Cryptography
One solution to this problem is visual cryptography. If we can use two displays from two different manufacturers and have them combine information visually, then we can build a chat device where no single component sees both halves of the message!
In this scheme, each device displays an image that is, on its own, indistinguishable from random. But when the images are XORed together, the plaintext is revealed. It’s a visual implementation of a one-time pad.
This idea has been around for a while. There is a great 2003 paper by Tuyls et al. called Visual Crypto Displays Enabling Secure Communications, where they do everything I do in this blog post and much more, including some analysis on how to achieve authenticity even if an attacker can modify the contents of a display.
First Attempt (Transparent OLEDs)
Before I learned about the LCD trick at the top of this post, I googled around for transparent displays and found these teeny transparent OLED modules sold by Sparkfun. Stacking OLED displays gives the visual OR operation, not the visual XOR operation, because the light just passes through.
It turns out you can create visual XOR from visual OR using little checkerboard patterns. A friend pointed out that this same technique is used in a voting scheme by David Chaum, except with paper instead of displays! From there I learned that this scheme goes back to (at least) Moni Naor and Adi Shamir in 1994.
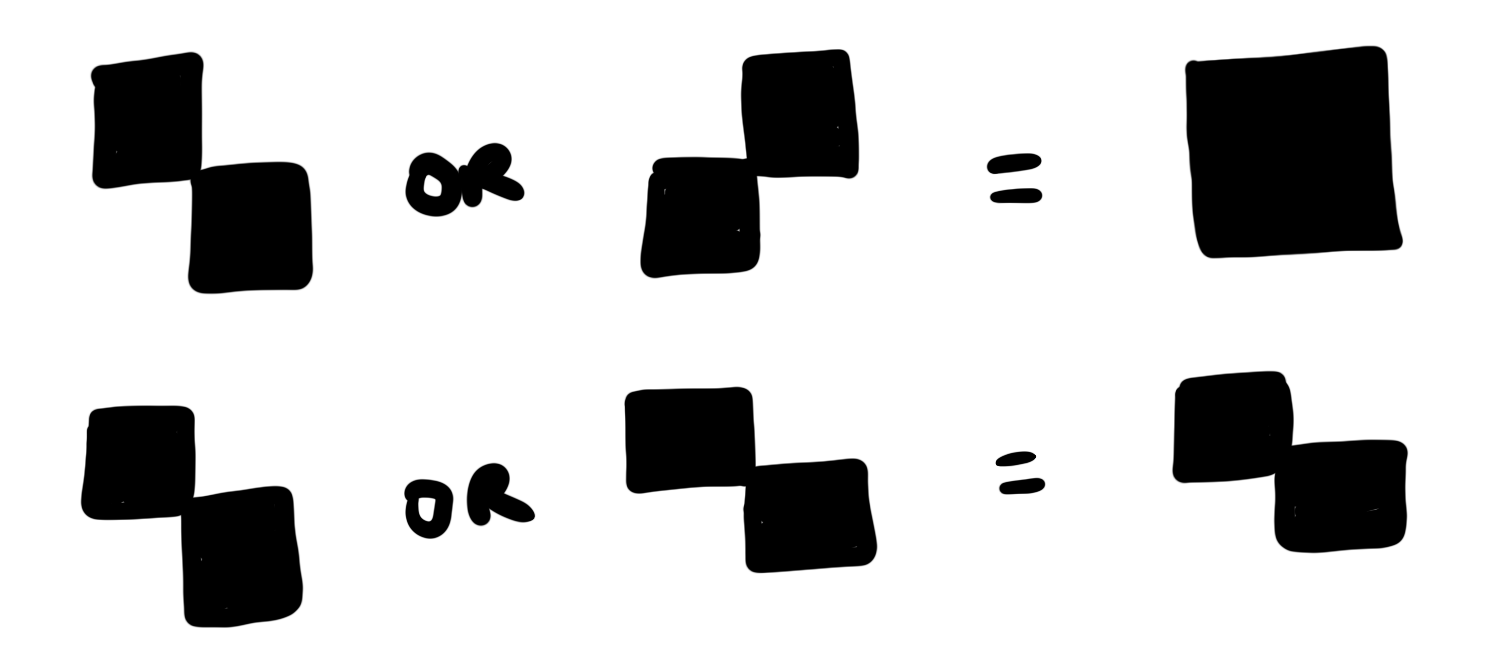

Second Attempt (LCDs)
LCD stands for Liquid Crystal Display. As the name suggests, LCDs use a material called a liquid crystal.
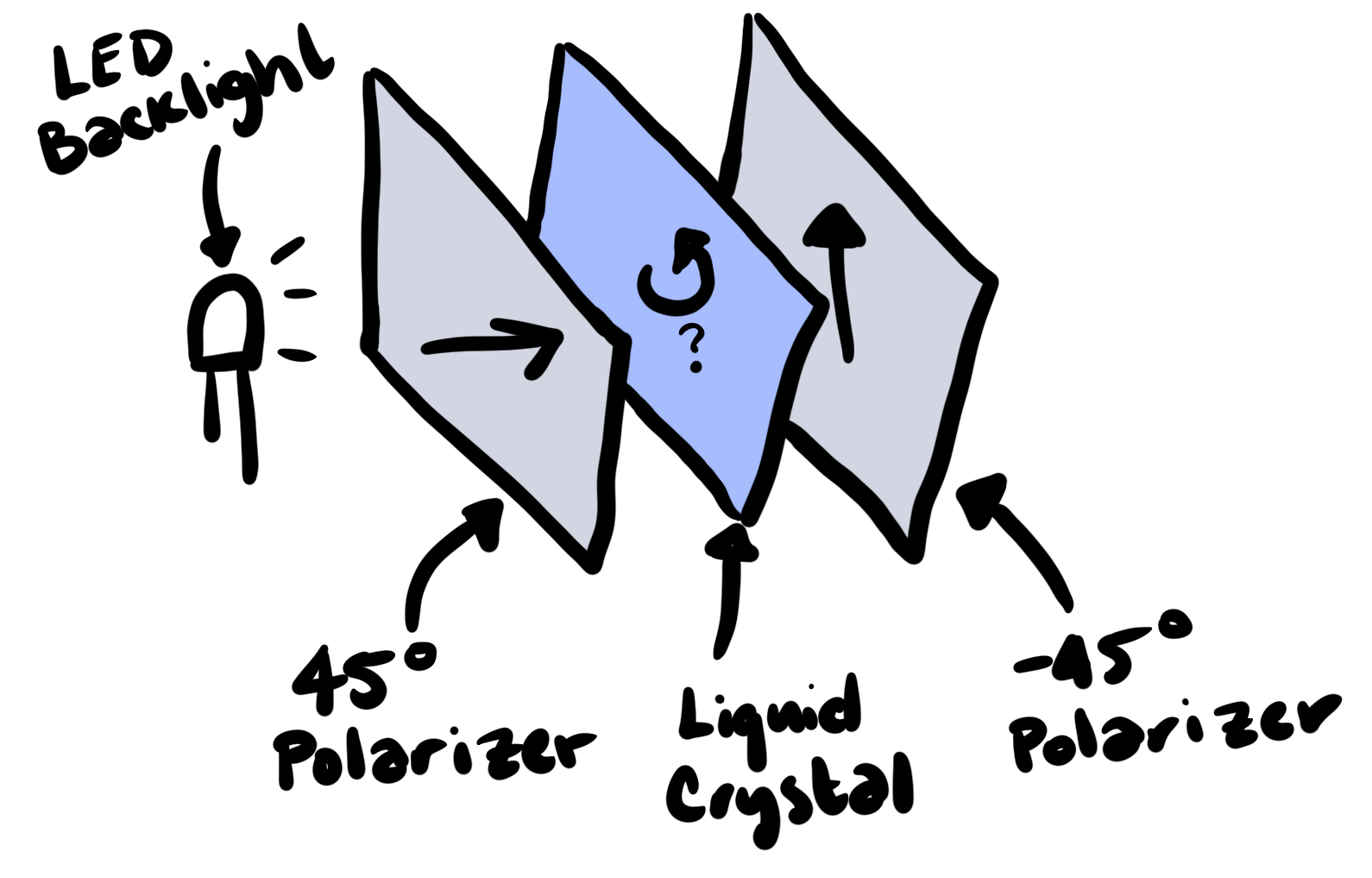
Twisted nematic liquid crystal displays work like this: when no voltage is applied across their liquid crystal layer, a helical structure forms, and the polarization of light shining through is rotated by some amount (on my LCDs, this is either 90 degrees or -90 degrees – I haven’t experimented to figure out which). When a large enough voltage is applied, the helical structure straightens out, and light passes through unchanged.
By putting a polarizing filter on either side of this liquid crystal layer, with the two filters rotated 90 degrees relative to one another, an LCD can selectively block light from passing through by raising or lowering the voltage.
So a normal LCD looks something like this:
But by peeling off the front polarizing layer from two LCDs, we can construct a display that looks like this:
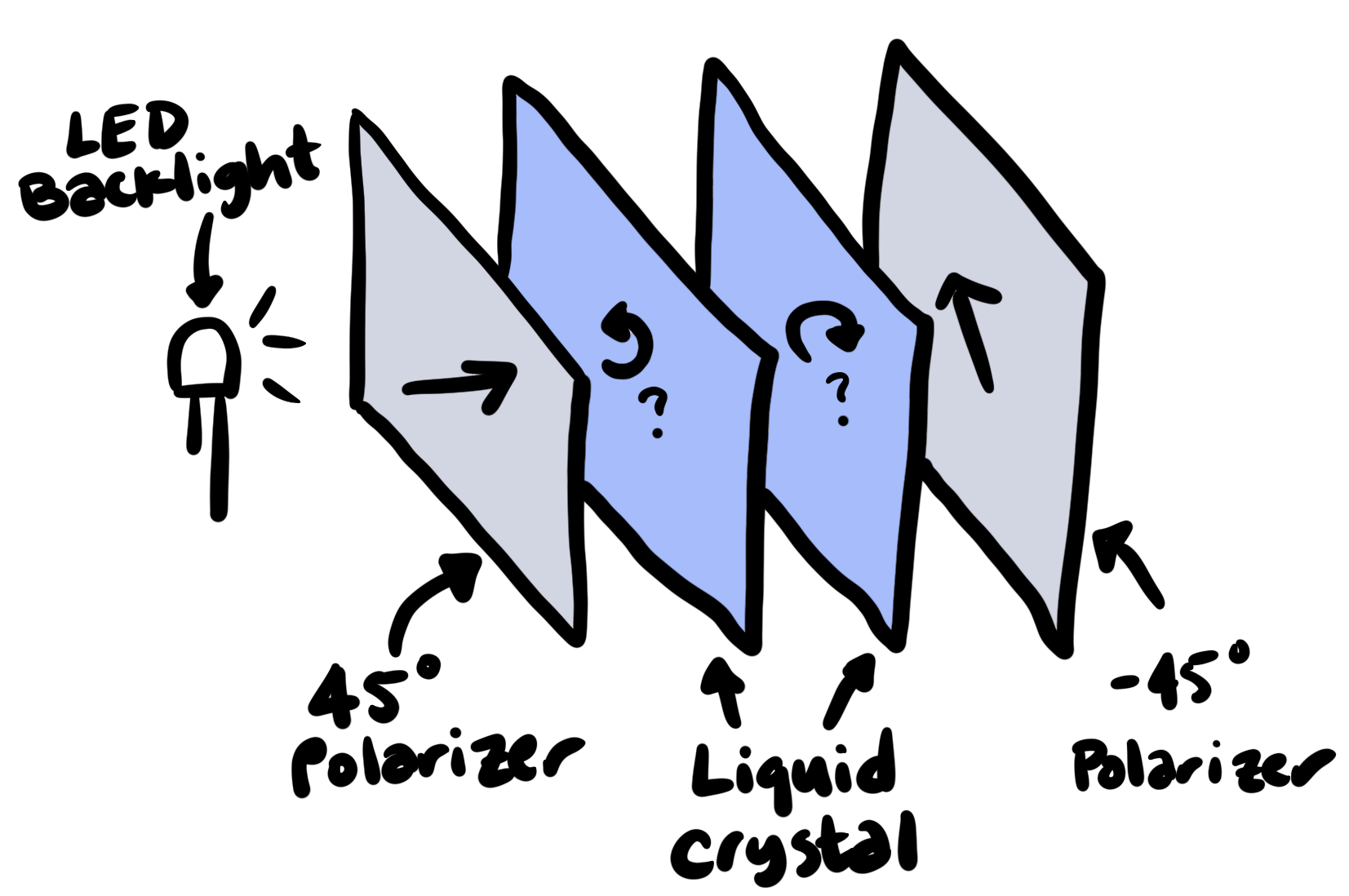
With this setup, the displays now perform the XOR operation! For a given pixel in some position on both displays:
- If both pixels are off, the polarization of incoming light is twisted by 90 degrees and then by -90 degrees, and so is blocked by the second polarizer.
- If exactly one of the pixels is off, the polarization of incoming light is twisted once by either 90 degrees or -90 degrees, and so passes through the second polarizer.
- If both pixels are on, light passes through the liquid crystal layers without rotating, and so is blocked by the second polarizer.
Once I figured out a design, actually putting it together was straightforward. I used two LCD modules from Adafruit, peeled off the front polarizers from both displays, removed the backlight from one display, and placed them front-to-front:
These LCD modules come apart super easily. The only hiccup I ran into was that I was shipped driver boards with the wrong firmware!
Phones
I want a secure communications device – something that only does simple chat, and doesn’t contain things like a web browser or ImageMagick. Secure chat apps like Signal are pretty good, but they usually run on smartphones, which consistently contain crazy-ass bugs that let remote adversaries completely take over your device. We have all of these great cryptographic protocols, but no easy way to use them securely!
Fortunately, there are some projects trying to address this problem. I’m really excited about Betrusted, which aims to build what is essentially a secure enclave with a keyboard, screen, and external untrusted networking component. This is excellent – we can remove entire classes of vulnerability by communicating with untrusted components over simple, easy-to-audit protocols.
But I have to wonder: without sacrificing usability, can we get one step more paranoid than devices like Betrusted? Can we have a device that is more secure than the weakest link in its supply chain?
(If you’re working on a secure communications device, please reach out!)





